This was a really fun project! Peering inside chips is mesmerizing – it reveals an intricate, nanoscale world of circuits and patterns, turning technology into art. Since the PS4 is now over 10 years old, and this information is common inside the scene – I thought I would share some images.

The PS4 does not encrypt the bootrom or efuses at rest. So they can be extracted using common imaging techniques (ie scanning electron microscope). The AM32 bootrom (LM32 variant) loads a second bootloader called the secure loader, which starts the rest of the system. The Secure Asset Management Unit (SAMU), a separate security co-processor, has all the goodies. The SAMU works together with the Crypto-Co Processor (CCP).

The bootrom was analyzed to discover fault injection locations.

If you dump a consoles efuses, combined with the flashdump, you can derive all the necessary certs/keys. Do you remember Xbox 360 KeyVaults?
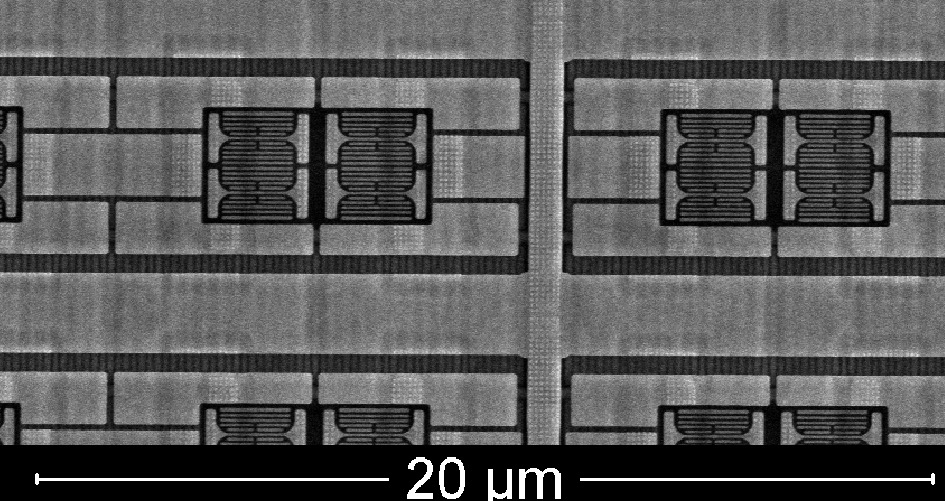
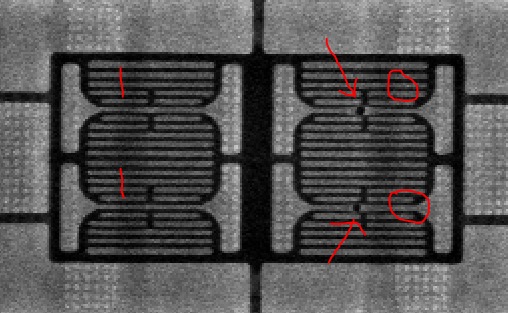
The price of imaging is cheap, but delayering can be expensive and takes specific equipment – like a 5 axis polishing machine. The technician must keep the sample planar while removing more than ten copper layers. All in all, these days the whole process will run you about $4k, probably less if done in China.
It is very plausible that some console hacking groups have found ways to dump fuses while still keeping the console intact. It amazes me the absurd bugs people find in Sony/AMD systems. For example, the CCP bug flatz shared or the fail0verflow PSVR FIGO authentication bug. I haven’t followed PS5 hacking but I read their hypervisor implementation was broken via sleep mode? You never know until you look hard enough.
Leave a Reply